- Determining Security Threats Through Information Flow Analysis
- Future Renewable Electric Energy Delivery and Management (FREEDM) Systems Center
- Secure Algorithms for Cyber-Physical Systems
- A Framework for Complexity Management in Virtual Forward Operating Base Camps
- Crafting a Human-Centric Environment to Support Human Health Needs
- Securing Smart Grid by Understanding Communications Infrastructure Dependencies
- BISON: Bio-Inspired Approach to Robust Wireless Sensor Networking
- SPANDAN: Scalable Parallel Algorithms for Network Dynamics Analysis
Determining Security Threats Through Information Flow Analysis
Determining Security Threats Through Information Flow Analysis
Security needs to move beyond the Fortress Mentality of Firewalls
INVESTIGATORS
Bruce McMillin (PI)
FUNDING SOURCE
National Institute of Standards and Technology
PROJECT DESCRIPTION
Providing Cyber-Physical System (CPS) security goes beyond traditional IT/enterprise cybersecurity and beyond purely physical security to combine both into Cyber-Physical Security. In CPSs, threats can arise through both the cyber and physical aspects, in combination. Moreover, in a CPS, ideas of high and low and inside and outside no longer represent modern systems; security domains can overlap. This proposal extends work in information flow analysis to detect the possibility of confidentiality leakages and integrity attacks, develop tools for assessment, and provide design parameters for reducing risk among security partitions of a CPS. The proposed work will be measured against developed use cases from NIST and the Smart Grid Interoperability Panel.
PUBLICATIONS
- “Modeling and reasoning about the security of drive-by-wire automobile systems,” Gerry Howser and Bruce McMillin, International Journal of Critical Infrastructure Protection, Elsevier 2012, DOI: 10.1016/j.ijcip.2012.09.001.
- “Mitigating Event Confidentiality Violations in Smart Grids: An Information Flow Security-based Approach,” Thoshitha Gamage, Thomas Roth, Bruce McMillin and Mariesa Crow, IEEE Transactions on Smart Grid, Vol. 4, No. 3, September 2013, pp. 1227-1234, DOI:10.1109/TSG.2013.2243924
- “Information Flow Quantification Framework for Cyber Physical System with Constrained Resources," Li Feng; McMillin, B., in Computer Software and Applications Conference (COMPSAC), 2015 IEEE 39th Annual , vol.2, no., pp.50-59, 1-5 July 2015,
10.1109/COMPSAC.2015.92 - “Quantification of Information Flow in a Smart Grid,” Li Feng and Bruce McMillin, Computer Software and Applications Conference Workshops (COMPSACW), 2014 IEEE 38th International, 21-25 July 2014, pp.140-145,10.1109/COMPSACW.2014.27.
- “A Modal Model of Stuxnet Attacks on Cyber-physical Systems: A Matter of Trust,” Gerald Howser and Bruce McMillin, Software Security and Reliability, 2014 Eighth International Conference on, June 30 2014-July 2 2014, pp.225-234,
10.1109/SERE.2014.36.
Future Renewable Electric Energy Delivery and Management (FREEDM) Systems Center
Future Renewable Electric Energy Delivery and Management (FREEDM) Systems Center
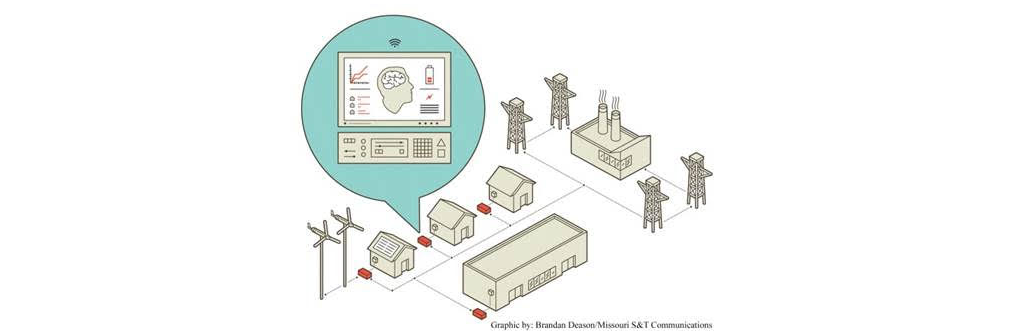 Peer-to-Peer Managed Microgrid
Peer-to-Peer Managed Microgrid
INVESTIGATORS
Bruce McMillin (PI), Mariesa Crow, Jonathan Kimball, Mehdi Ferdowsi (co-PIs)
FUNDING SOURCE
NSF
PROJECT DESCRIPTION
The mission of the ERC for FREEDM Systems is to develop the fundamental and enabling technology to foster a revolution in innovation and technology in the electric power and renewable energy industries. For intellectual merit the work has yielded numerous publications, in advancing distributed energy management, system modeling, and security (a selected list is [20],[28],[62]–[68]) and has advanced the electric smart grid effort significantly past its current state. Extensive broader impacts include outreach to industry, consortia, and K-12 science and undergraduate and under-represented group mentoring. Specifically, FREEDM has contributed to the Smart Grid Interoperability Panel and the National Institute of Standards and Technology Cyber-Physical Systems Public Working Group (2014-) and NISTiR 7628, Security and Privacy for the Smart Grid. In particular, the FREEDM project's outreach makes distributed energy management and the advanced smart grid understandable by the general population.
PUBLICATIONS
- "Towards formal verification of smart grid distributed intelligence: FREEDM case," Patil, Sandeep; Zhabelova, Gulnara; Vyatkin, Valeriy; McMillin, Bruce, in Industrial Electronics Society, IECON 2015 - 41st Annual Conference of the IEEE , vol., no., pp.003974-003979, 9-12 Nov. 2015, 10.1109/IECON.2015.7392719
- “Implementation of FREEDM Smart Grid distributed load balancing using IEC 61499 Function Blocks,” Sandeep Patil, Valeriy Vyatkin, Bruce McMillin, Proceedings of the 39th Annual Conference of the IEEE Industrial Electronics Society, Vienna, Austria, Industrial Electronics Society, pp.8154-8159, 10-13 Nov. 2013,10.1109/IECON.2013.6700497.
- “The Effects of Network Link Unreliability For Leader Election Algorithm in a Smart Grid System,” Stephen Jackson and Bruce McMillin, Seventh CRITIS Conference on Critical Information Infrastructures Security, Springer, LNCS 7722, Hämmerli, Bernhard; Kalstad Svendsen, Nils; Lopez, Javier (Eds.), Lillehammer, Norway, September 17-18, 2012, pp. 59-70, 10.1007/978-3-642-41485-5_6
- "Distributed Grid Intelligence for future microgrid with renewable sources and storage," Fanjun Meng; Akella, R.; Crow, M.L.; McMillin, B.; North American Power Symposium (NAPS), 2010 , 26-28 Sept. 2010, 10.1109/NAPS.2010.5618963.
- “Distributed Power Balancing for the FREEDM System,” Ravi C Akella, Derek Ditch, Fanjun Meng, Bruce McMillin, and Mariesa Crow, The 1st Smart Grid Computing Conference, Gaithersburg, MD, Oct 3-6, 2010, pp. 7 12, 10.1109/SMARTGRID.2010.5622003.
Secure Algorithms for Cyber-Physical Systems
Secure Algorithms for Cyber-Physical Systems
INVESTIGATORS
Jonathan Kimball (PI), Bruce McMillin (co-PI)
FUNDING SOURCE
NSF
PROJECT DESCRIPTION
The objective of this proposal is to formulate a novel methodology for creating secure algorithms in cyber-physical systems and to develop metrics for evaluating the security of composed systems. Cyber-physical systems are composed of interconnected, semi-autonomous devices. The inherently open nature of a CPS implies a susceptibility to attacks that differ fundamentally from conventional cyber-attacks. CPS-specific attack vectors exist as purely cyber, cyber-enabled physical attacks, and physically enabled cyber-attacks. As such, the endpoints may be fundamentally unsecurable (such as the sensed information from physical resources) or may be compromised (as in computational resources). Creating a secure communications channel between two nodes is inadequate if one of the endpoints of the communication is insecure. Therefore, new methodologies are needed to ensure that the system is protected in the presence of open information flows from physical resources and possibly malicious entities inside the system.
The proposed approach relies on the interconnected nature of the cyber and physical aspects to ensure that information exchanges are trustworthy. Any action taken by any entity in the system should project onto the various subsystems in a consistent way. For example, in a power system, if an entity claims to be generating a certain amount of power (within the cyber realm), then the flows and voltages on the grid (within the physical realm) should reflect that generation level. The projections may be used to evaluate the trustworthiness of each entity.
The first objective is to formulate a methodology that incorporates knowledge from both the cyber and physical domains into a distributed algorithm to ensure the trustworthiness, thus security, of the composed system. The second objective is to derive metrics for security. Both objectives rest on logical invariants that express correctness. The invariants either check the validity of a local action or the accuracy of remote data. They may be used as guards against an action, or may be incorporated into a dynamic reputation-based algorithm. As a testbed, a multilateral energy system on an electrical network will be studied. Preliminary studies of this system have resulted in algorithms that isolate malicious nodes within the context of a single algorithm, using a reputation metric that compares cyber information flows to physically measurable signals. The work will be extended to other algorithms and other related power systems, a generalizable framework will be developed, and more complete metrics will be derived.
PUBLICATIONS
- “Physical Attestation in the Smart Grid for Distributed State Verification,” Tom Roth and Bruce McMillin, IEEE Transactions on Dependable and Secure Computing, 2016, DOI/10.1109/TDSC.2016.2577021.
- “Breaking Nondeducible Attacks on the Smart Grid,” Thomas Roth and Bruce McMillin, Seventh CRITIS Conference on Critical Information Infrastructures Security, Springer, LNCS 7722, Hämmerli, Bernhard; Kalstad Svendsen, Nils; Lopez, Javier (Eds.), Lillehammer, Norway, September 17-18, 2012, Published 2013, pp. 80-91, 10.1007/978-3-642-41485-5_8.
- “Physical Attestation of Cyber Processes in the Smart Grid,” Tom Roth and Bruce McMillin, Eighth CRITIS Conference on Critical Information Infrastructures Security, , Amsterdam, Netherlands, September 16-18, 2013, Lecture Notes in Computer Science 8328, Springer, pp. 96-107, 10.1007/978-3-319-03964-0_9.
- “Using Information Flow Methods to Analyze the Security of Cyber-Physical Systems," Gerry Howser and Bruce McMillin, Computer, 2016 (to appear).
- T. Roth and B. McMillin, "Physical attestation in the smart grid for distributed state verification," IEEE Transactions on Dependable and Secure Computing, vol. PP, no. 99, pp. 1{1, 2017.
- F. Love and B. McMillin, "Breaking implicit trust in point-of-care medical technology: A cyber-physical attestation approach," in 2017 IEEE 41st Annual Computer Software and Applications Conference (COMPSAC), vol. 02, July 2017, pp. 242{247.
- G. Howser and B. McMillin, "Using information- ow methods to analyze the security of cyber-physical systems," Computer, vol. 50, no. 4, pp. 17{26, April 2017.
- U. Kanteti and B. McMillin, "Multiple security domain model of a vehicle in an automated vehicle system," in Proceedings of the Eleventh IFIP WG 11.10 International Conference on Critical Infrastructure Protection. Arlington, VA: Springer, 2017.
- S. C. Jackson and B. McMillin, "Application of congestion notifications in a cyber-physical system," in 2017 IEEE 22nd Pacifc Rim International Symposium on Dependable Computing (PRDC), Jan 2017, pp. 165{174.
- P. R. Dunaka and B. McMillin, "Cyber-physical security of a chemical plant," in 2017 IEEE 18th International Symposium on High Assurance Systems Engineering (HASE), Jan 2017, pp. 33{40.
- A. Thudimilla and B. McMillin, "Multiple security domain nondeducibility air traffic surveillance systems," in 2017 IEEE 18th International Symposium on High Assurance Systems Engineering (HASE), Jan 2017, pp. 136{139.
- J. A. Mueller and J. Kimball, "An Efficient Method of Determining Operating Points of Droop Controlled Microgrids," IEEE Transactions on Energy Conversion, vol. PP, no. 99, pp. 1{1, 2017.
- J. A. Mueller and J. W. Kimball, "Accurate Energy Use Estimation for Nonintrusive Load Monitoring in Systems of Known Devices," IEEE Transactions on Smart Grid, vol. PP, no. 99, pp. 1{1, 2017.
- G. Mpembele and J. Kimball, "Analysis of a standalone microgrid stability using generic Markov jump linear systems," in 2017 IEEE Power and Energy Conference at Illinois (PECI), Feb. 2017, pp. 1{8.
- W. Zhang and J. W. Kimball, "DC-DC Converter Based Photovoltaic Simulator with a Double Current Mode Controller," IEEE Transactions on Power Electronics, vol. PP, no. 99, pp. 1{1, 2017.
A Framework for Complexity Management in Virtual Forward Operating Base Camps
A Framework for Complexity Management in Virtual Forward Operating Base Camps
INVESTIGATORS
Steven Corns (PI), cornss@mst.edu, 573-341-6367; Suzanna Long, (Co-PI), longsuz@mst.edu, Mariesa Crow, (Co-PI), crow@mst.edu
FUNDING SOURCE
U.S. Army Corps of Engineers and Department of Engineering Management and Systems Engineering at Missouri S&T.
PROJECT DESCRIPTION
This project provides a holistic approach to base camp layout and design. A framework has been developed to incorporate multiple models and simulations with information sharing between these models. This provides a method to couple the information related to the base camp systems to capture the second, third, and higher order effects brought about by changes in these systems. By accounting for these complex relationships it is possible to create an accurate representation of base camp resource usage. Several tools were developed to create and enable the interfaces both between model types and between models and decision makers/system users.
PUBLICATIONS
- “Dynamic Mathematical Model Framework of Complex Utility and Logistics System Interactions using Object-Oriented Approach for Forward Operating Bases,” Bhanuchander Poreddy, Steven Corns, Suzanna Long, and Ahmet Soylemezoglu, (2015), accepted to Engineering Management Journal.
- “A SysML Framework for Modeling Contingency Basing,” Dustin Nottage, Steven M. Corns, Ahmet Soylemezoglu, and Kurt Kinnevan, (2015), Systems Engineering, DOI: 10.1002/sys.21297.
- “An Automated Forward Operating Base Electrical Distribution System Simulator,” Onur Kavechi, Mariesa L. Crow, and Steven M. Corns (2012), North American Power Symposium (NAPS), Digital Object Identifier 10.1109/NAPS.2012.6336351.
- “SysML Profiling for Handling Army Base Camp Planning,” Dustin S. Nottage and Steven M. Corns (2011) Complex Adaptive Systems Conference, Procedia Computer Science, Volume 6, pp. 63-68.
Crafting a Human-Centric Environment to Support Human Health Needs
Crafting a Human-Centric Environment to Support Human Health Needs
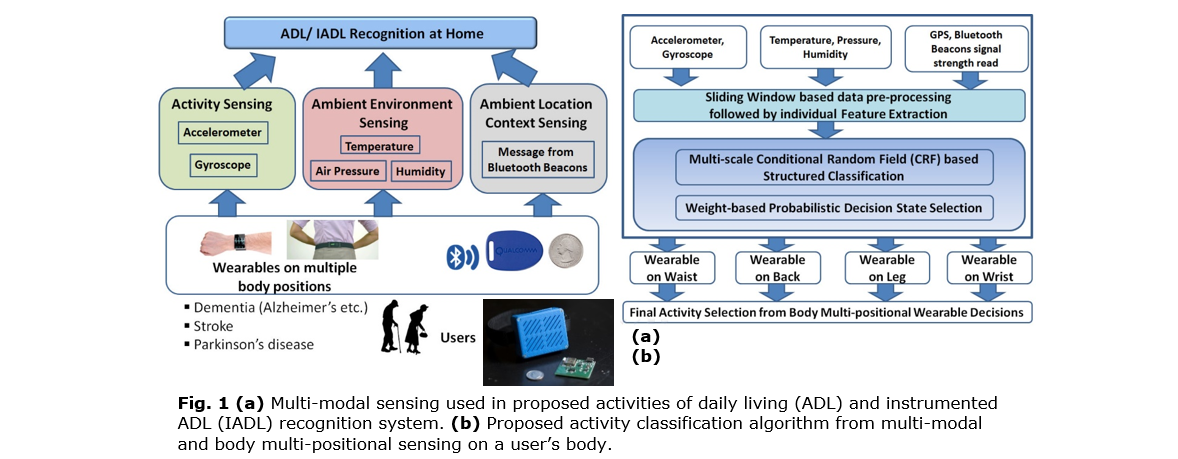
INVESTIGATORS
Sajal K. Das (sdas@mst.edu, 573-341-7708)
FUNDING SOURCE
National Science Foundation (Smart and Connected Health Program)
PROJECT DESCRIPTION
The goal of this project is to design, implement, and evaluate in-home techniques for generating reports of activities and social interactions that are useful for monitoring wellbeing and for automating intervention strategies for persons with dementia. The plan is to design machine learning techniques that make effective use of sensor data to perform automated activity monitoring and prompting-based interventions that are beneficial for the residents as well as for their caregivers and family. The environment is human-centric because it learns information about its human residents and uses this information to provide activity-aware monitoring and intervention services. By transforming everyday environments into smart environments, many older adults with cognitive and physical impairment can lead independent lives in their own homes. A key component of this project is an evaluation of the technologies in actual homes with volunteer older adults and thus will assess the technologies for acceptance with the target population.
PUBLICATIONS
- “Quality and Context-Aware Smart Healthcare,” N. Roy, C. Julien, A. Misra, and S. K. Das, IEEE Systems, Man and Cybernetics Magazine, 2(2): 15-25 (2016).
- “Determining Quality- and Energy-Aware Multiple Contexts in Pervasive Computing Environments,” N. Roy, A. Misra, S. K. Das, and C. Julien, IEEE/ACM Transactions on Networking, 24(5): 3026-3042 (2016).
- “Incentive Mechanisms for Participatory Sensing: Survey and Research Challenges” F. Restuccia, S. K. Das, and J. Payton, ACM Transactions on Sensor Networks, 12(2): 2016.
- “Multi-modal Wearable Sensing for Fine-grained Activity Recognition in Healthcare,” D. De, P. Bharti, S. K. Das, and S. Chellappan, IEEE Internet Computing (special issue on Small Wearable Internet), 19(5): 26-35 (2015).
- “A-Wristocracy: Deep Learning on Wrist-worn Sensing for Recognition of User Complex Activities”, P. Vepakommaz, D. De, S. K. Das, and S. Bhansal, Proceedings of 12th IEEE Annual Body Sensor Networks Conference (BSN). MIT, Cambridge (2015).
- “Care-Chair: Sedentary Activities and Health Assessment with Smart Sensing on Chair Backrest,” R. Kumar, A. Bayliff, D. De, A. Evans, S. K. Das, and M. Makos, Proceedings of 2nd IEEE International Conference on Smart Computing (2016).
- “An Adaptive Bayesian System for Context-Aware Data Fusion in Smart Environments,” A. De Paola, P. Ferraro, S. Gaglio, G. Lo Re and S. K. Das, IEEE Transactions on Mobile Computing, accepted to appear (2016).
Securing Smart Grid by Understanding Communications Infrastructure Dependencies
Securing Smart Grid by Understanding Communications Infrastructure Dependencies
INVESTIGATORS
Sajal K. Das (sdas@mst.edu, 573-341-7708), Mariesa Crow and Simone Silvestri
FUNDING SOURCE
National Science Foundation (Cyber-Physical Systems Program)
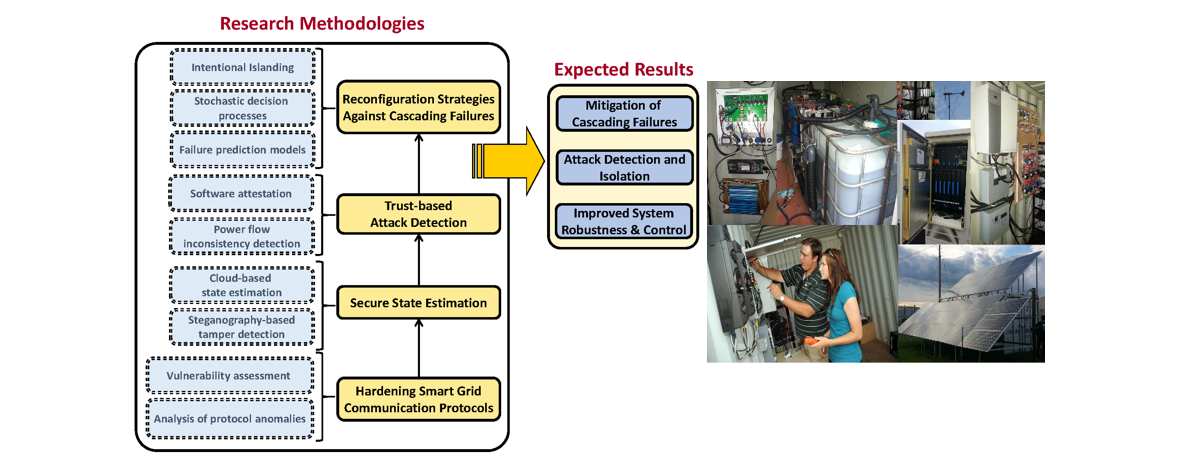
PROJECT DESCRIPTION
The objective of this collaborative project is to understand, study and analyze in a holistic manner the vulnerabilities of smart grid system due to intricate interactions with the communication networks. Specific goas include: (i) investigating a wide variety of attacks, misconfiguration, malfunctioning, and failure scenarios in the communications networks, and characterizing their impacts on the smart grid; and (ii) designing a multi-level security framework based on robust state estimation and trust model that hardens the grid against malfunctions and attacks from the communications side, thus preventing cascade failures.
PUBLICATIONS
- “Managing Contingencies in Smart Grids via the Internet of Things,” S. Ciavarella, J.-Y. Joo, and S. Silvestri, IEEE Transactions on Smart Grid, 7(4): 2134-2141 (2016).
- “Survey of Security Advances in Smart Grid: A Data Driven Approach,” S. Tan, D. De, W.-Z. Song, J. Yang, and S. K. Das, IEEE Communications Surveys and Tutorials, to appear (2016).
- “Towards a Realistic Model for Failure Propagation in Interdependent Networks,” A. Sturaro, S. Silvestri, M. Conti, and S. K. Das, Proceedings of International Conference on Computing, Networking and Communications, Hawaii (2016).
- “Reliable Energy-Efficient Uplink Transmission for Neighborhood Area Networks in Smart Grid,” F. Ye, Y. Qian, R. Q. Hu, and S. K. Das, IEEE Transactions on Smart Grid (special issue on Cyber Physical Systems and Security for Smart Grid), 6(5): 2179-2188 (2015).
- “JAMMY: A Distributed and Self-Adaptive Solution against Selective Jamming Attack in TDMA WSNs,” M. Tiloca, D. De Guglielmo, G. Dini, G. Anastasi, and S. K. Das, IEEE Transactions on Dependable and Secure Computing, to appear (2016).
- “Incentive Mechanism Design for Heterogeneous Crowdsourcing Using All-Pay Contests,” T. Luo, S. S. Kanhere, S. K. Das, and H.-P. Tan, IEEE Transactions on Mobile Computing, 15(9): 2234-2246 (2016).
- “An Efficient Security Protocol for Advanced Metering Infrastructure in Smart Grid,” Y. Yan, R. Q. Hu, S. K. Das, H. Sharif, and Y. Qian, IEEE Network, 27(4): 1-10 (2013).
BISON: Bio-Inspired Approach to Robust Wireless Sensor Networking
BISON: Bio-Inspired Approach to Robust Wireless Sensor Networking

INVESTIGATORS
Sajal K. Das (sdas@mst.edu, 573-341-7708)
FUNDING SOURCE
National Science Foundation
PROJECT DESCRIPTION
Organisms adapt to external perturbations through optimized structure of their gene regulatory networks (GRNs). In the long-term, the state transition network of a GRN converges to a set of attractors that make the organism resilient to removal or functional impairment of genes. In wireless sensor networks (WSNs), such attractors refer to a group of sensors serving as sink nodes for packets sent over multiple hops. This project maps such attractor based genomic robustness onto WSNs to infer optimal topologies and routing strategies that mitigate both sensor failure and a noisy wireless channel. This is being achieved by conducting experiments in silico gene by simulating the functional removal of a gene from sample GRNs, to understand the dynamics of the attractor state space. This information is next used to design WSN topologies and routing protocols that are resilient to network uncertainty, node breakdown and compromise. This project also pursues the design of optimal wiring rules between sensors in a robust WSN that guarantees maximum probability of successful packet transmission under a given routing strategy. Validation and testing are accomplished on real life WSN testbeds.
PUBLICATIONS
- “DRIH-MAC: A Distributed Receiver-Initiated Harvesting-aware MAC for Nano-Networks,” S. Mohrehkesh, M. Weigle, S. K. Das, IEEE Transactions on Molecular, Biological and Multi-Scale Communications, 1(1): 97-110 (2015).
- “Energy-efficient Randomized Switching for Maximizing Lifetime in Tree-based Wireless Sensor Networks,” Sk. K. A. Imon, A. Khan, M. Di Francesco, and S. K Das, IEEE/ACM Transactions on Networking, 23(5): 1401-1415 (2015).
- “Exploiting gene regulatory networks for robust wireless sensor networking,” M. Nazi, M. Raj, Di Francesco, P. Ghosh, and S. K. Das. In Proceedings of IEEE Global Communications Conference (GlobeCom): Selected Areas in Communications: Molecular, Biological and Multi-Scale Communications), San Diego (2015).
- “Leveraging the Robustness of Genetic Networks: A Case Study on Bio-inspired Wireless Sensor Network Topologies,” B. K Kamapantula, A. Abdelzaher, P. Ghosh, M. Mayo, E. J Perkins, and S. K Das, Journal of Ambient Intelligence and Humanized Computing, 5(3):323–339 (2014).
- “Deployment of Robust Wireless Sensor Networks using Gene Regulatory Networks: An Isomorphism-based Approach,” A. Nazi, M. Raj, M. Di Francesco, P. Ghosh, and S. K Das, Pervasive and Mobile Computing, 13:246–257 (2014).
- “Qos-aware Geographic Opportunistic Routing in Wireless Sensor Networks,” L. Cheng, J. Niu, J. Cao, S. K Das, and Y. Gu, IEEE Transactions on Parallel and Distributed Systems, 25(7):1864–1875 (2014).
- “Analysis and Optimization of a Protocol for Mobile Element Discovery in Sensor Networks,” F. Restuccia, G. Anastasi, M. Conti, and S. K Das, IEEE Transactions on Mobile Computing, 13(9):1942–1954 (2014).
SPANDAN: Scalable Parallel Algorithms for Network Dynamics Analysis
SPANDAN: Scalable Parallel Algorithms for Network Dynamics Analysis
INVESTIGATORS
Sajal K. Das (sdas@mst.edu, 573-341-7708)
FUNDING SOURCE
National Science Foundation
PROJECT DESCRIPTION
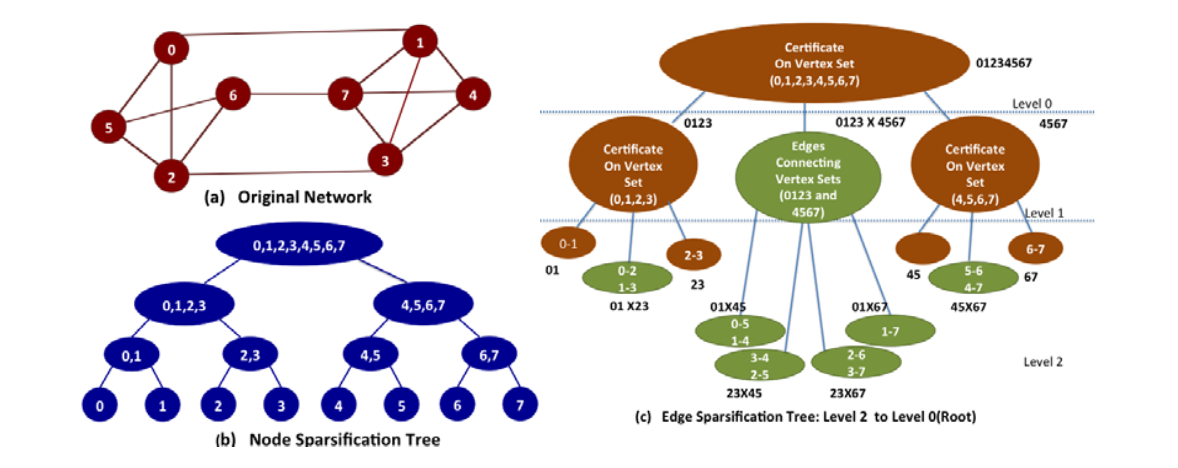
The goal of this project is to create a novel architecture-independent framework for designing efficient, portable and scalable parallel algorithms for analyzing large-scale dynamic networks, such as social networks, biological networks, and disaster networks. The basic idea is to exploit graph sparsification techniques to divide the network into sparse subgraphs (certificates) that form the leaves of a sparsification tree. This innovative approach leads to the design and analysis of efficient parallel algorithms for updating dynamic networks, and reduction of memory latency associated with parallelizing unstructured data. Specifically, parallel algorithms will be designed for maintaining network topological characteristics and updating influential vertices and communities. The portability and performance of algorithms will be demonstrated via implementation on distributed memory clusters, shared memory multicores, and massively multithreaded parallel computers.
PUBLICATIONS
- “PIS: A Multi-dimensional Routing Protocol for Socially-aware Networking,” F. Xia, L. Liu, B. Jedari, and S. K. Das, IEEE Transactions on Mobile Computing, 15(9): 2234-2246, Sept 2016.
- “Overhead Control with Reliable Transmission of Popular Packets in Ad-Hoc Social Networks,” F. Xia, H. B. Liaqat, J. Deng, J. Wan, and S. K. Das, IEEE Transactions on Vehicular Technology, 65(9): 7647-7661 (2016).
- “Application of Graph Sparsification in Developing Parallel Algorithms for Updating Dynamic Networks,” S. Srinivasan, S. K. Das and S. Bhowmick, Graph Algorithm Building Blocks Workshop at IEEE International Symposium on Parallel and Distributed Processing Systems, Chicago (2016).
- “Leveraging Contact Pattern to Predict Future Contact Pattern in Mobile Networks,” S. Das, S. K. Das, and S. Ghosh, Proceedings of 8th International Workshop on Hot Topics in Planet-scale mobile computing and online Social networking (HotPOST’16), Paderborn, Germany (2016).
- “RescuePal: a Smartphone-based System to Discover People in Emergency Scenarios,” F. Restuccia, S. K. Das, S. C. Thandu, and S. Chellappan, Proceedings of 5th Workshop on Internet of Things: Smart Objects and Systems (IoT-SoS), Coimbra, Portugal (2016).
- “Interference-free Scheduling with Minimum Latency in Cluster-based Wireless Sensor Networks,” A. Navarra, C. M. Pinotti, M. Di Francesco, and S. K. Das, Wireless Networks, 21(7): 2395-2411 (2015).
- “Leveraging Network Structure in Centrality Evaluation of Large Scale Networks,” S. Das and S. K. Das, Proceedings of 40th Annual IEEE Conference on Local Computer Networks (LCN), Clearwater Beach, FL, pp. 579-586, Oct 2015.
- “E-DARWIN: Energy Aware Disaster Recovery Network using WiFi Tethering,” M. Raj, K. Kant, and S. K. Das, Proceedings 23rd International Conference on Computer Communications and Networks, Shanghai, China, pp. 1-8 (2014).

Follow Intelligent Systems Center